Diferencia entre revisiones de «Spreadsheets»
Sin resumen de edición |
Sin resumen de edición |
||
| (No se muestran 8 ediciones intermedias de 3 usuarios) | |||
| Línea 6: | Línea 6: | ||
*[http://wl500g.info/showthread.php?14170-Exploring-WL500gP-hardware-expansion-interfacing-possibilities http://wl500g.info/showthread.php?14170-Exploring-WL500gP-hardware-expansion-interfacing-possibilities] | *[http://wl500g.info/showthread.php?14170-Exploring-WL500gP-hardware-expansion-interfacing-possibilities http://wl500g.info/showthread.php?14170-Exploring-WL500gP-hardware-expansion-interfacing-possibilities] | ||
*[http://wl500g.info/showthread.php?14170-Exploring-WL500gP-hardware-expansion-interfacing-possibilities&p=102889#post102889 http://wl500g.info/showthread.php?14170-Exploring-WL500gP-hardware-expansion-interfacing-possibilities&p=102889#post102889] | *[http://wl500g.info/showthread.php?14170-Exploring-WL500gP-hardware-expansion-interfacing-possibilities&p=102889#post102889 http://wl500g.info/showthread.php?14170-Exploring-WL500gP-hardware-expansion-interfacing-possibilities&p=102889#post102889] | ||
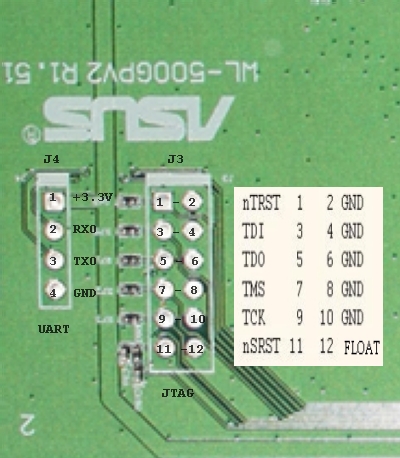
<div class="imagelink_somename">[[File:ASUS-V2-jtag1.jpg]]<br/></div><div class="imagelink_somename"><br/></div> | <div class="imagelink_somename">[[File:ASUS-V2-jtag1.jpg]]<br/></div><div class="imagelink_somename"><br/></div><div class="imagelink_somename">Otra cosa muy interesante es que este router parece permitir algunas posibilidades de expansion :)</div> | ||
== buspirate cheatsheet == | |||
[http://wiki.openwrt.org/toh/asus/wl500gp http://wiki.openwrt.org/toh/asus/wl500gp] | |||
this router uses: 115200 baud and 8-n-1 (no conectar +V) | |||
*screen /dev/ttyUSB0 115200 8N1 | |||
*UART: m, 3 | |||
*[http://dangerousprototypes.com/bus-pirate-manual/bus-pirate-uart-guide/ http://dangerousprototypes.com/bus-pirate-manual/bus-pirate-uart-guide/] | |||
*[http://www.electricoding.com/2014/08/10/getting-started-with-bus-pirate-3-6-under-linux/ http://www.electricoding.com/2014/08/10/getting-started-with-bus-pirate-3-6-under-linux/] | |||
*[http://hackaday.com/2008/11/19/how-to-the-bus-pirate-universal-serial-interface/ http://hackaday.com/2008/11/19/how-to-the-bus-pirate-universal-serial-interface/] | |||
*[https://blog.malwarebytes.org/hackedunpacked/2014/02/uart-root-shell-on-commercial-devices/ https://blog.malwarebytes.org/hackedunpacked/2014/02/uart-root-shell-on-commercial-devices/] | |||
*[http://wiki.openwrt.org/doc/howto/generic.debrick http://wiki.openwrt.org/doc/howto/generic.debrick] | |||
* | |||
== Otras formas == | |||
*Intentando conectarse por puerto serial el router no responde. | |||
*Parece que el chip Broadcom 5354 responde con JTAG, pero bus-pirate no da una forma amigable de reflashear el chip. A continuación otras formas de flashearlo vía JTAG. | |||
*[http://www.dd-wrt.com/wiki/index.php/Recover_from_a_Bad_Flash http://www.dd-wrt.com/wiki/index.php/Recover_from_a_Bad_Flash] | |||
*[http://wiki.openwrt.org/doc/hardware/port.jtag http://wiki.openwrt.org/doc/hardware/port.jtag] | |||
* http://wl500g.info/showthread.php?5298-How-do-I-solder-a-JTAG-connector-to-Asus-WL-500/page2 | |||
Revisión actual - 15:23 22 ene 2015
Router ASUS WL-500GPV2
Alguien ha brickeado el ASUS, asi que estamos mirando como restaurarlo. Nos podemos conectar al bicho por el UART o JTAG:
- http://wl500g.info/showthread.php?5298-How-do-I-solder-a-JTAG-connector-to-Asus-WL-500/page2
- http://wl500g.info/showthread.php?14170-Exploring-WL500gP-hardware-expansion-interfacing-possibilities
- http://wl500g.info/showthread.php?14170-Exploring-WL500gP-hardware-expansion-interfacing-possibilities&p=102889#post102889
Otra cosa muy interesante es que este router parece permitir algunas posibilidades de expansion :)
buspirate cheatsheet
http://wiki.openwrt.org/toh/asus/wl500gp
this router uses: 115200 baud and 8-n-1 (no conectar +V)
- screen /dev/ttyUSB0 115200 8N1
- UART: m, 3
- http://dangerousprototypes.com/bus-pirate-manual/bus-pirate-uart-guide/
- http://www.electricoding.com/2014/08/10/getting-started-with-bus-pirate-3-6-under-linux/
- http://hackaday.com/2008/11/19/how-to-the-bus-pirate-universal-serial-interface/
- https://blog.malwarebytes.org/hackedunpacked/2014/02/uart-root-shell-on-commercial-devices/
- http://wiki.openwrt.org/doc/howto/generic.debrick
Otras formas
- Intentando conectarse por puerto serial el router no responde.
- Parece que el chip Broadcom 5354 responde con JTAG, pero bus-pirate no da una forma amigable de reflashear el chip. A continuación otras formas de flashearlo vía JTAG.